Last week the internet security firm Kaspersky Lab released a report on a highly-successful group of cybercriminals who targeted banks and may have stolen up to a billion across 100 financial institutions worldwide. While Kaspersky Labs did not name the victimized organizations, the report indicates they were mostly located in China, Russia and the United… Read More »
Android & PC Tie For First Place In Malware
A report published last week by Alcatel-Lucent revealed malware on mobile devices has caught up to the infection rate on traditional PCs. The report was created by the telecommunications company’s Motive Security Labs and used data compiled from fixed and mobile networks using their Motive Security Guardian software. The software is deployed in networks around… Read More »
What Are Drone Operators All Waiting For?
Last week I talked about drone operators who don’t follow the rules. This week I’ll talk about legal drones, existing regulations and the new rules that are due out soon. Commercial Use Current FAA regulations prohibit the commercial use of drones, but companies can apply for a special permit. According to Reuters, as of February… Read More »
How Can We Prevent The Next White House Drone Crash?
Current Federal Aviation Administration regulations require civilian drones to stay under 400 feet in altitude and at least five miles from airports and other restricted areas. Unfortunately, not all drone operators follow the regulations. Drones at the White House On Monday, January 26th at 3:02 AM a Secret Service officer on duty at the White House… Read More »
Deep Dark Web Of The Internet Iceberg
The World Wide Web is a vast and always changing network of web pages. In the early days of the web there were no search engines, and people relied on finding information using pages with long lists of HTML links. It was cumbersome and links were often outdated. The development of automated search engines made… Read More »
My Phone Is Held Hostage By Ransomware, Now What?
Ransomware is a type of malware that holds your data hostage. It has been a problem with computers for many years, but it’s only recently started showing up on mobile devices. When you activate the program or app, it blocks you from accessing the data on the device and displays a message demanding payment by… Read More »
Can The FBI Attract Ethical Hackers?
In today’s online world, cyber attacks can be nearly as devastating as traditional warfare. In addition to cyber terrorism, hackers have stolen identification and credit card information from millions of Americans in cyber attacks on large businesses. Local law enforcement often doesn’t have the skills or manpower to handle these cyber crimes, and jurisdiction becomes… Read More »
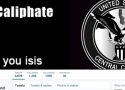
ISIS Hacks CENTCOM And You Are Next
On Monday, January 12th, the official Twitter account & YouTube channel for US Central Command or CENTCOM were hacked by ISIS supporters. Pro-ISIS propaganda appeared on @CENTCOM Twitter homepage warning “American Soldiers, we are coming, watch your back. ISIS.” @CyberCaliphate account is currently suspended but claims to have hacked the US Central Command Twitter account. Besides the… Read More »
- « Previous Page
- 1
- …
- 11
- 12
- 13
- 14
- 15
- …
- 20
- Next Page »