Right now most civilian drones are owned by hobbyists for recreational use, but many companies are exploring commercial uses. Drones have already been used for shooting nature documentaries and commercials, aerial surveys on remote properties, checking on crops for farmers and even delivering pizza. They have the potential to revolutionize many aspects of our daily… Read More »
LastPass Hacked And Why I Have Never Used It
I have always felt the concept of LastPass as well as other password managers makes sense for users that would otherwise create simple ‘easy to remember’ passwords as opposed to long strong complex passwords with a password manager. Surely, having numerous passwords in the cloud encrypted is better than jotted down on a sticky note that… Read More »
Global Governments Attempt to Peel The Onion Router
Tor has been embraced by lawful and unlawful users alike. It helps those who value their online privacy and dissidents who live in countries with oppressive governments, but it also provides ways for cyber criminals, terrorists and other bad guys to avoid identification. This has made breaking Tor’s anonymity a top priority for government agencies… Read More »
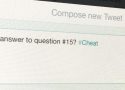
Teachers Have New Enemy In War On Cheating
Back in the days before the Internet, ethically-challenged students could make a quick buck by selling copied test questions to other students who still needed to take the test. Now students are trading copied tests on the Internet using social media instead of in the hallways. In the old days, most tests were not standardized… Read More »
Why Healthcare Hacking Has Become Big Business
As banks and large retailers have taken steps to harden their networks, hackers have turned their attention to healthcare providers. Just recently, Premera announced a breach that took place last year may have exposed the personal and financial data of approximately 11 million customers. Last month, the nation’s second largest health insurance company reported the information… Read More »
How Easy Is It For Hackers To Jack The Tower?
Earlier this month the Government Accountability Office issued a 46-page report outlining security vulnerabilities in critical Federal Aviation Administration (FAA) systems. The report concerns the national airspace system (NAS) used to track and direct public and private aircraft. Many of these issues are common in all types of organizations, so look over the FAA’s list of… Read More »
The Hidden Privacy Upside of Net Neutrality
On February 26th the Federal Communications Commission voted in favor of stronger net neutrality rules. The vote reclassifies both wired and wireless broadband internet service providers (ISPs) as utilities under Title II of the Communications Act of 1934. Most of the media attention has focused on the ruling barring ISPs from blocking or prioritizing… Read More »
- « Previous Page
- 1
- …
- 10
- 11
- 12
- 13
- 14
- …
- 20
- Next Page »