What do you get for the person that has everything? Gift cards, while impersonal, do make gifting easy for those of us that are too busy or disinclined to search for that perfect gift. Hackers have gotten into the act of ‘carding’ but not like you think.
What is Carding?
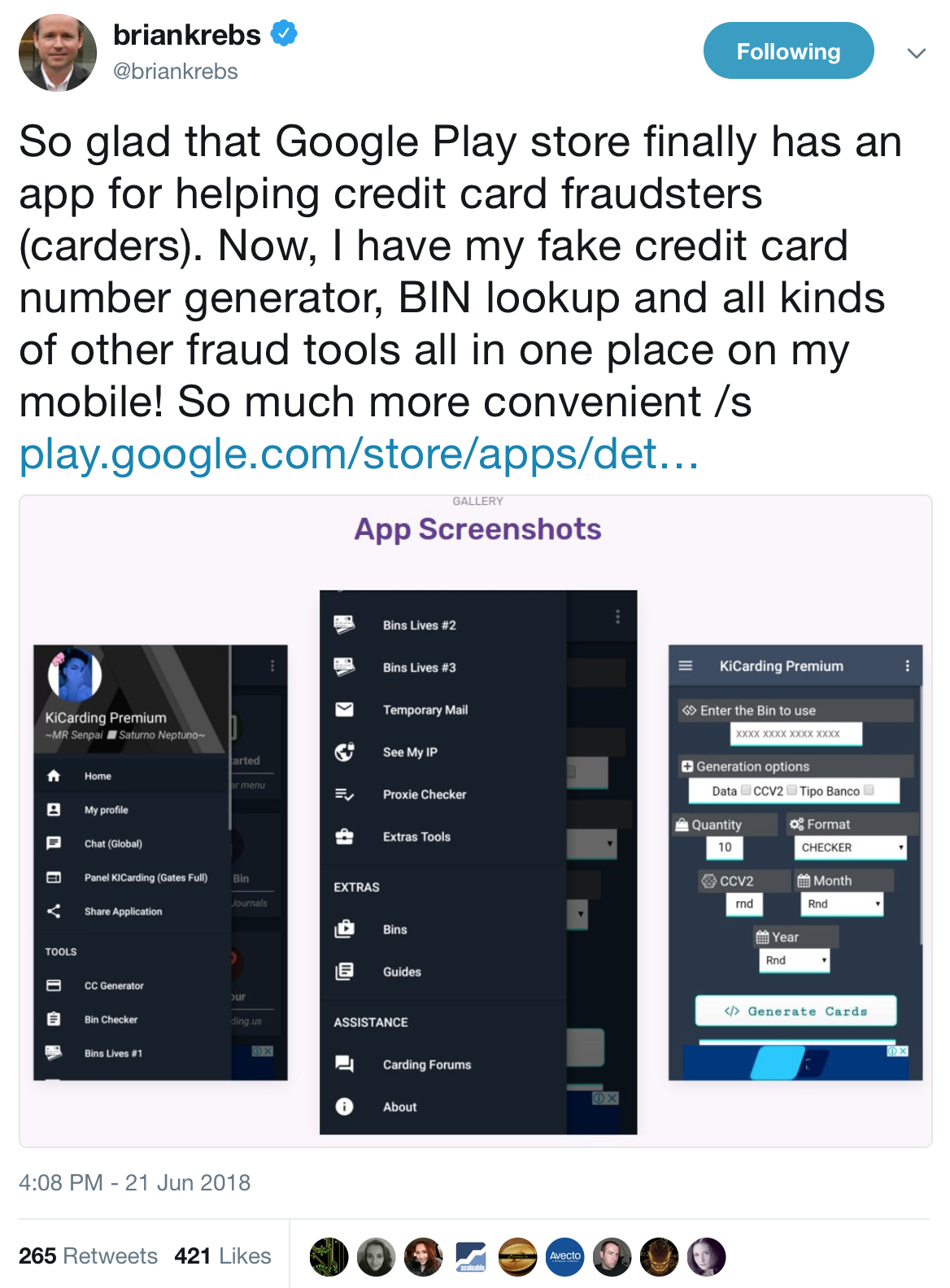
Carding is when a stolen credit card is used to charge for pre-paid gift cards. A hacker will either steal or purchases stolen credit cards (usually on the Dark Web) and then purchase store-branded gift cards. These gift cards are then sold to consumers (on Ebay for example) to purchase goods or then re-sold sold for cash. Many of these gift cards are used to purchase high value electronics such as televisions since those goods can easily be resold but that hasn’t stopped many cyber thieves from also selling small $5 Amazon cards by the truckload as well. If the carder purchases a gift card for a retailer such as Target or Amazon, they may use a 3rd party to actually receive the goods and then have the shipment directed to other locations. This can distance and limit the attention that might be drawn to the carder which anonymous hackers love. And of course, carders often sell their fraudulently obtained electronics on the Dark Web providing further anonymity and fully completing their criminal cycle.
Credit card fraud continues to threaten consumers as hackers evolve their techniques to get into our wallets. Credit card fraud globally is expected to grow billion of dollars every year.
Who are these carders?
Creating layers and complexity is nothing new to cyber thieves. Many hackers implant misdirection or subtle clues into their malware code. Many others steal consumers’ identity and then play a waiting game. The more time that transpires between the initial theft and the sale or use of that data, the more difficult it is for consumers to remember or trace back to the initial theft. Dark Web anonymity requires the TOR browser and a VPN to disguise the visitor’s identity and location so carders are already well versed in criminal subterfuge. Suffice it to say, carders (and most hackers) work in dark corners actively covering up their tracks making them much harder to bring to justice than your run-of-the-mill thief.
Where are all of these compromised cards coming from?
With so many data breaches in the headlines from Target to Home Depot and hundreds of companies in between, there are literally millions of compromised credit cards circulating on the Dark Web. And even though credit cards are typically and quickly cancelled upon being lost or stolen, cyber thieves will occasionally test the stolen card information to see if it still works. This is accomplished by submitting small purchase requests over the Internet.
Another huge source of stolen card numbers come from something every driver does. Gas pump skimmers have plagued credit and debit card users for years now but the ubiquity of low cost bluetooth skimmers and brazen hackers have led to a national epidemic of credit card fraud. Hundreds of gas stations currently continue to contain hidden skimmers that record thousands of credit card numbers daily. These numbers (and their associated security PINs) continue to fetch a high price across the Dark Web.
How can I stay safe?
I’m afraid there is no silver bullet to keeping your credit card safe from carders or any other type of identity thief. I can recommend that you never use your credit card but that’s not realistic, convenient or even good for your credit score. I will say that you should minimize your card footprint. That means you should not have your credit card(s) spread across multiple services such as Venmo, Paypal, Samsung Pay, Apple Pay, Google Pay, etc. because these services are somewhat redundant. Some are more secure than others but none are invulnerable to user or server level hacks so you will greatly reduce your chances of credit card fraud just by only using one service for example. Of course the same goes for retail stores, e-commerce sites, streaming services and even gas stations but try telling that to a millennial. If Chip and PIN is offered at POS terminal, use it; if it’s not, leave that store and do not return until they respect your privacy and security by updating to the latest POS security protocols.
Of course there are also skimmers of all types and their perpetrators out there waiting for you to sink your card into them. This also means that there are tools to fight these skimmer scams used by law enforcement but it’s up to consumers to stay safe by keeping credit and debit card use to a minimum while staying alert to any possible fraud.
- Stalking threats still very real for TV actress - 10/16/2024
- CrowdStuck thanks to CrowdStrike - 07/25/2024
- AT&T breach too big to ignore - 07/14/2024


Leave a Reply
You must be logged in to post a comment.