BVS CEO & Cyber Security Expert, Scott Schober provides security details on Inside Edition
Last week’s leak of confidential celebrity photos has focused renewed public attention on the security risks of storing data in the cloud. The photos were originally posted on a seedy Internet site by an anonymous user, then reposted to other disreputable sites. Some of the victimized celebrities released said the images were authentic but deleted a long time ago, others stated theirs were faked.
The original poster claimed the photos were taken from hacked iCloud accounts. A few simple account changes could have kept the victims’ accounts safe. Today we’ll look at what users can do to protect their cloud data.
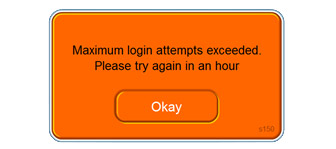
Limit Login Attempts
It’s common for banks and other high-security web sites to lock user accounts after a few tries. If someone fails to enter the correct password, after 5 to 10 attempts the account locks and the user must call to have the account reset or wait a specific period of time before they can try again. Some sites make you turn on the feature and control the maximum number of attempts. Check the settings on your account and contact support if you have concerns.
In this case, iCloud did not have a limit on the number of attempts. Hackers could use readily-available software to try an unlimited number of passwords. Since the nude photo story broke, Apple has patched this vulnerability, but hackers can still use this vulnerability at many sites holding confidential information.
Enable Two-Factor Authentication
Many hacks occur when the victim’s email account is compromised. The hacker can find sites where the victim might be a member by reading old messages, then go to the site and request a password reset. If a site uses single-factor authentication by email, the hacker can then reset the victim’s passwords and access their accounts on those sites.
Many cloud-based services and secure sites offer two-factor authentication. For example, when a user requests a password change, the service may send an authentication email to their address and text a security code to their cell phone. Two-factor authentication is more secure, because a hacker would need access to both the victim’s email and their cell phone.
Two-factor authentication adds an extra step to the process, so some sites offer it as an option. Users must enable it manually. iCloud had it as an option, but at the time the pictures were released it was not enabled by default.
Select Secure Security Questions
When a user sets up their account, the site may ask them to pick a security question in case they forget their password. Common questions include “What high school did you attend?” or “What was the name of your first pet?” If everyone in the user’s social network knows they went to Riverdale High and their first pet was Fluffy, the user should select a different question. Better yet, create unique passwords or gibberish answers to the questions. This will ensure no one but you will ever be able to get past this security checkpoint. Just be sure to remember or note your answers somewhere for future reference.
Deleted Doesn’t Mean Gone
Just like deleting a file from a computer doesn’t remove it from the hard drive, deleting a picture from a phone doesn’t necessarily mean it’s gone forever. With many cloud services, the device will automatically upload pictures and deleting them off the device may not delete them from the cloud. Another potential source of concern is the server backups. Some companies store backups for years, and hackers could access those backups if they’re not adequately protected.
Ultimately, keeping sensitive data and photos private is up to both the user and the company running the service. For the moment, it’s best to remember online security is not absolute. If you want to keep data private, keep it offline.
[yop_poll id=”3″]
- Stalking threats still very real for TV actress - 10/16/2024
- CrowdStuck thanks to CrowdStrike - 07/25/2024
- AT&T breach too big to ignore - 07/14/2024


Leave a Reply
You must be logged in to post a comment.