The October 17th launch of the iPhone 6 in China was overshadowed by a hack attack aimed at stealing Chinese users’ iCloud login information. Less than 24 hours after the release of the highly-anticipated smartphone, anti-censorship advocates in China tweeted about the attack. On the 20th they posted more information on a blog at greatfire.org accusing the Chinese government of being behind the attack.
How did the attack take place?
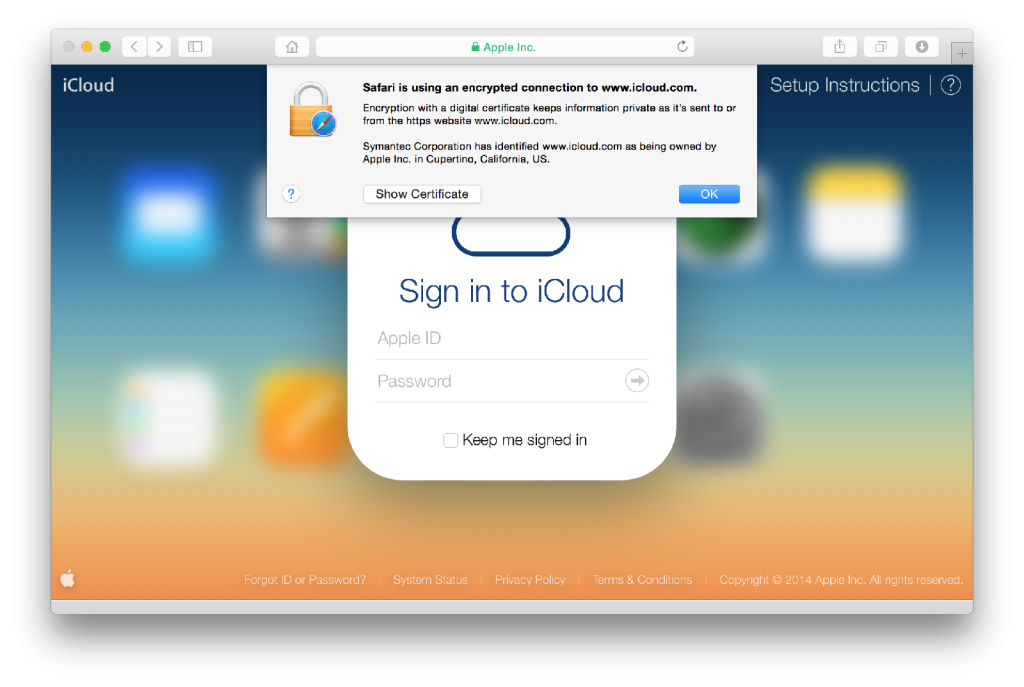
The hackers used a black hat technique known as a man-in-the-middle (MITM) attack. When a computer or device accesses a secured web page through the browser, the remote server provides a security certificate verifying it is the correct site. MITM attacks reroute the Internet traffic through another server that uses a fake certificate to fool the device into thinking it is communicating directly with the original site. When a user puts in their login name and password, the middleman can intercept the information.
Similar MITM attacks have occurred recently against Chinese users of Google, Github, Microsoft and Yahoo. The Apple MITM was the most serious, as it was nationwide in scope and occurred while many users were setting up their new devices. The hack only affected a single iCloud server IP address, and Apple was able to block the attack by directing Internet traffic to a different IP address.
Why do security experts believe the Chinese government is involved?
Like other aspects of the media, the Internet is heavily censored in China. The Chinese government regularly spies on private citizens looking for signs of political dissent. Apple stores iCloud information outside of China, out of the direct control of the Chinese government.
Since the Chinese government owns and operates the country’s telecommunications and wireless services, the attack may be an attempt to get around officials not being able to access iCloud information directly. It could also be in response to the iPhone 6’s increased security safeguards and the recent anti-government political demonstrations in Hong Kong.
How can you protect yourself against MITM attacks?
MITM attacks are difficult to orchestrate on such a large scale without deep access to public telecommunications networks. The latest hack may have been limited to Apple users in China, but smaller-scale MITM can happen anywhere. Here are some easy ways you can protect your information.
- Use two-factor authentication when possible. Without the second piece of information, attackers won’t be able to access your account even if they have your username and password.
- Watch for browser pop-ups alerting you to an expired or invalid certificate when you visit a secure site. If you receive a notification, view the certificate and verify the information is correct.
- Do not access sensitive sites over open WiFi networks without using a virtual private network (VPN). MITM attacks are much easier to pull off over open wireless networks, and some criminals even set up their own WiFi hotspots just to steal data. A VPN prevents these attacks by setting up an encrypted connection between your device and the VPN server.
- Stalking threats still very real for TV actress - 10/16/2024
- CrowdStuck thanks to CrowdStrike - 07/25/2024
- AT&T breach too big to ignore - 07/14/2024


Leave a Reply
You must be logged in to post a comment.